Overview
Law and enforcement agencies use mobile CDR that is also known as call detail records of mobile number, IMEI and tower dump for investigation of crime. This is advanced and technical method of investigation. Mobile service providers provide CDR to law and enforcement agencies. This is a huge data usually in excel or text format which is impossible to analyze manually. CDR Analysis Software is a solution provided by PurpleRadiance for analysis of call detail record. Various useful reports are generated using this software which helps law and enforcement agencies in investigation of crime.
Relations between calls of different persons or groups can be found out within seconds. This software does many active calculations over tower dump to get relations of calls or people operating at different locations. Finding common numbers, IMEI and IMSI of different people and different mobile towers or locations can be done with the help of this software. This software represents data graphically for better understanding. Social network analysis of suspects can be done using this software. All reports are very easy and simple to understand. This software is also known as CDR Data Analysis Software or Tower Dump Analysis Software.
Mobile number analysis
Mobile companies capture all calls, SMS, and data session information with called party, date, time, duration and latitude and longitude details. Law enforcement agencies use this information for the investigation of one or more target persons.
What we can get out of Mobile number analysis?
- Generate a comprehensive report of calling patterns that gives glimpse of the target person’s behavior.
- Frequently visited a location and night out location.
- Find contact details of family members and close friends.
- Track movement on google map.
- Find common friends and common locations.
- CC Summary – Common callers summary
- CELL ID Summary – Call locations summary
- IMEI Summary – Handsets used
- IMSI Summary
- Chart – Charts to visualize type of calls
- Usage – Handsets used in particular time
- Conference call
- FCLC – First call last call of a day
- FCLC Summary – First call last call summary
- FCLC OP – First call last call summary of other party
- Archives – Old relations of target number
- Archives Adv – Old relations of target number in whole database
- Extract – Important details of target number to summarize
- Map – Plotting route and call locations on Google maps
- Movements – Calls of target number with all details such as location address, other party details
- Route – Route used by target number
- Moving Calls – Moving calls of target number
- Roaming Summary – Different mobile circles (states) visited by target number
- Split Analysis – Analysis of calls of target number in different independent time frames
- Daily Called – Daily called other parties of target number
- Daily Called Adv – Daily called other parties of target number and dates
- Daily Location – Daily visited location by target number
- Daily Location Adv – Daily visited location by target number and dates
- Location Periodic – Calls location of target number in specific time
- Pattern Analysis – Calls pattern of target number
- Custom Pattern – Custom calling pattern of target number
- Links – Graphical representation of calls of target number
- Outgoing Calls – Outgoing calls of target number
- Incoming Calls – Incoming calls of target number
- Outgoing SMS – Outgoing SMS of target number
- Incoming SMS – Incoming SMS of target number
- Summary – Summary of all target numbers
- Chart – Charts to visualize type of calls
- Detailed Summary – Details of all target numbers
- Mixed Calls – Calls of target numbers with all details such as location address, other party details
- Map – Plotting route and call locations on Google maps
- Common Callers – Common other parties between all target numbers
- Shared Locations – Common locations between all target numbers
- Meeting Point – Meeting point of all target numbers
- IMEI Summary – Handsets used by all target numbers
- Internal Calls – Internal calling between all target numbers
- Numbers In CDR – Common other parties between at least two target numbers
- IMEI In CDR – Common handsets used between at least two target numbers
- Location In CDR – Common locations shared between at least two target numbers
- Relation – Graphical relation of all target numbers and other parties
- Relation Self – Graphical relation of all target numbers
- Pattern Analysis – Calls pattern of target numbers
- Custom Pattern – Custom calling pattern of target numbers
- Links – Graphical representation of calls of target number
- Outgoing Calls – Outgoing calls of target numbers
- Incoming Calls – Incoming calls of target numbers
- Outgoing SMS – Outgoing SMS of target numbers
- Incoming SMS – Incoming SMS of target numbers

IMEI analysis
Nowadays people change handset frequently and this trend is common in criminals to misguide officers. IMEI is known as International Mobile Equipment Identity which is unique to each handset. The IMEI is a 15-digit number that includes information about the origin, model, and a serial number of the device. If the officer knows IMEI he can easily reach to criminal by analyzing single and multiple IMEI CDR.
What we can get out of IMEI Analysis?
- Different sim cards used by a person.
- When and where a person has switched sim cards.
- Identification of different sim cards used to call friends, family and gang members.
- Track movement on google map.
- Target Number – Mobile numbers used in IMEI
- Chart – Charts to visualize type of calls
- CC Summary – Common callers summary of all numbers used in IMEI
- Archives Adv – Old relations of all numbers used in IMEI in whole database
- Usage – Mobile numbers used in particular time
- Roaming Summary – Different mobile circles (states) visited by IMEI
- Moving Calls – Moving calls of IMEI
- Summary Cell ID – Call locations summary of IMEI
- Common Callers – Common other parties of at least two mobile numbers used in IMEI
- Map – Plotting route and call locations on Google maps
- Movements – Calls of IMEI with all details such as location address, other party details
- Route – Route used by IMEI
- Detailed Summary – Summary of calls done by mobile numbers used in IMEI
- FCLC – First call last call of a day
- FCLC Summary – First call last call summary
- Daily Called – Daily called other parties of mobile numbers used in IMEI
- Daily Location – Daily visited location of mobile numbers used in IMEI
- Pattern Analysis – Calls pattern of mobile numbers used in IMEI
- Custom Pattern – Custom calling pattern of mobile numbers used in IMEI
- Links – Graphical representation of calls of mobile numbers used in IMEI
- Outgoing Calls – Outgoing calls of IMEI
- Incoming Calls – Incoming calls of IMEI
- Outgoing SMS – Outgoing SMS of IMEI
- Incoming SMS – Incoming SMS of IMEI
Subscriber detail record analysis
People use different sim cards to get maximum benefits from service providers offer. To activate new sim card user has to provide KYC documents. Law enforcement agencies use this information to get other information about the person.
What we can get out of Subscriber detail record analysis?
- Location of person.
- Number of sim cards purchased by person.
- Switched on and off date of sim cards.
- Support different types of SDR file uploading.
- Search by number.
- Search by name
- Search by address
- Search by KYC document details
- Find number of SIM cards register against particular name.

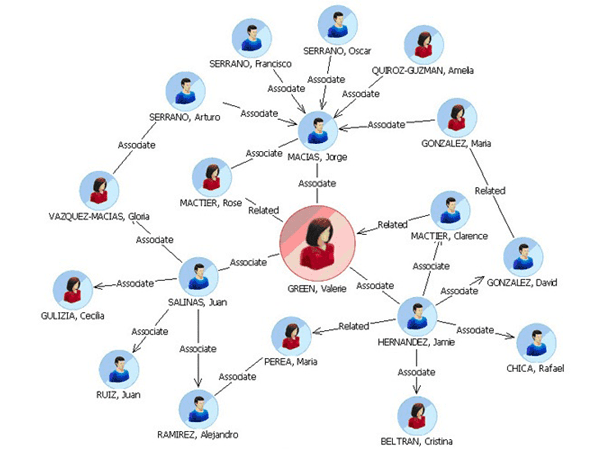
Social network analysis
In the era of social media, layman person also creates accounts on a different social media platform. Over the period of time people share enormous personal information like photos, thoughts about topic, likes, dislike and videos. Law enforcement agencies can harness this information to get intelligence out of OSINT.
What we can get out of Social network analysis?
- Person and his family members and friend’s photos.
- Video liked and shared by person.
- Thought about subject and people
- Number search on different social media sites.
- Twitter analysis.
- Youtube analysis.
- IP address search.
- Messenger analysis.
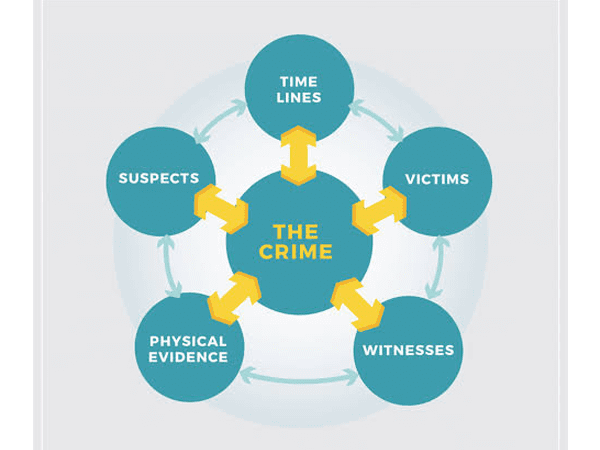
Case analysis
A person with a crime history can be identified, if any kind of presence is found in a similar type of crime or in a present investigation. This helps in narrowing the investigation towards the right path.
What we can get out of Case analysis?
- Person who is involved in multiple crimes.
- Number of persons involved in the crime
- The person who is executing crime and who is sitting somewhere else
- Case comparison.
- Case summary.
- Graphical relationship between different cases.
- Common mobile number.
- Common IMEI.
- Common other party.
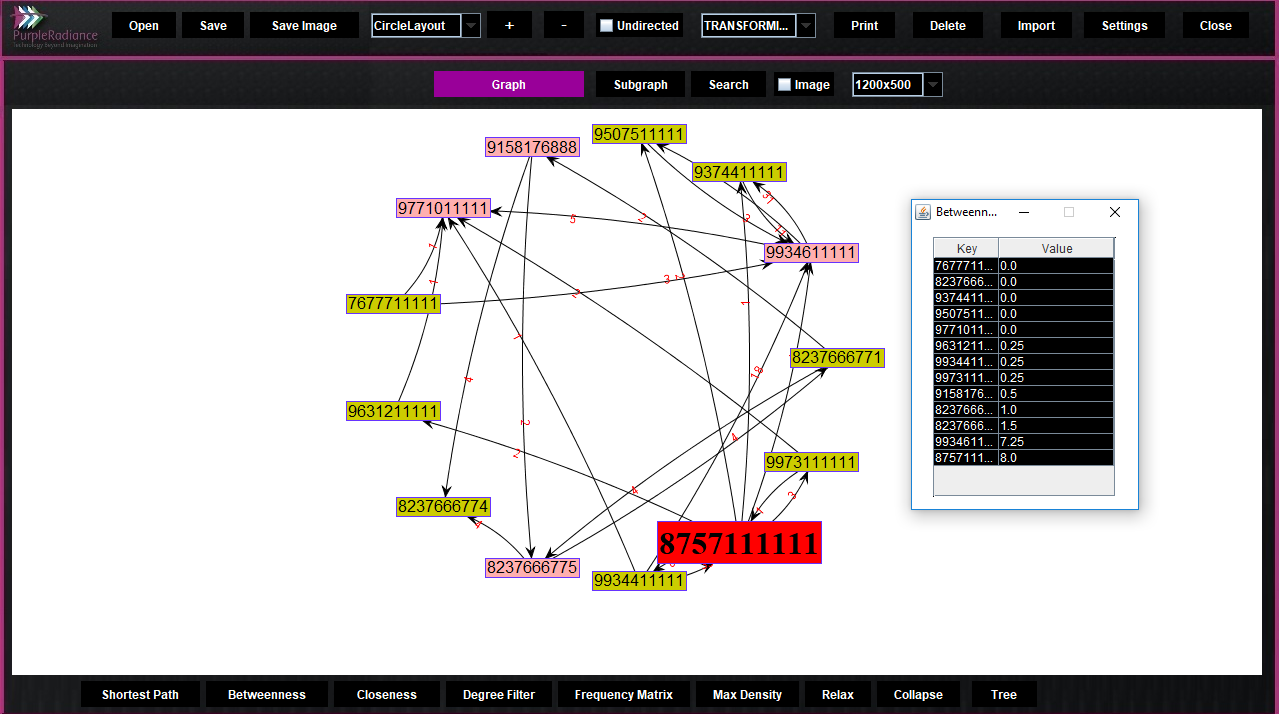
Link analysis
Images play important role in accelerating minds and giving solutions, which cannot be obtained by using theoretical solutions. Similarly, to find the relations among the people virtual representation plays important role.
What we can get out of Link analysis?
- Person who is operating criminal network.
- Person who is exchange the information between two or more criminal networks.
- Hierarchy within criminal network
- Accessibility of person to another person
- Data Representation with FR layout, static layout, circular layout and spring layout.
- Shortest path between to nodes.
- Betweenness in network.
- Closeness in network.
- Facilities to apply degree filter.
- Frequency matrix.
- Max density generator.
- Subgraph
- Export and import graph
IPDR analysis
Today’s generation can’t live without mobile data, they frequently access different social media applications and websites. When person use mobile data, provider assign dynamic IP to user’s device and capture data session information.
What we can get out of IPDR analysis?
- Location of person.
- Interested sites and applications.
- Mobile Number IP CDR analysis.
- IP CDR analysis.
- Destination IP domain detail.
- Cell track – Find out exact tower location with the help of Google maps, which avoids your cell tracking by going to spot.
- Cell IDs
- Advance SDR (Storm)
- Standalone Link Analysis
- Archive Old Cases
- Export Reports


Tower dump analysis
Mobile tower provides communication links between users. Whenever user initiate call it route through the tower. Tower capture information like calling user, called user, duration, date and time. If there are no clues Law enforcement agencies relies on tower data information. They find suspect persons using single or multiple towers data.
What we can get out of Tower dump analysis?
- Local person who lives within the vicinity of tower.
- Person who has visited to scene of offense first time.
- Person who has visited few days or few hours before the crime.
- Group of people those were present at scene of offense.
- Person continuously speaking with another person who is sitting somewhere else.
- Find the common person present at different locations.
- Summary – Summary of all calls done from tower
- Chart – Charts to visualize type of calls
- Archives – Old relations of target number
- Call Details – All calls done from tower with all details such as location address, other party details
- Under Tower Calls – Such calls where both numbers were present at tower location
- Common Mobile Number – Common mobile numbers between different towers
- Common IMEI – Common IMEI between different towers
- Common Other Party – Common other party between different towers
- Internal Callers – Internal calls between different towers
- Internal Numbers In Tower – Numbers in contact with different towers by being present at tower location or by making call from outside to tower location
- Groups – Calling groups formed in different towers
- Pattern Analysis – Calls pattern of tower
- Custom Pattern – Custom calling pattern of tower
- Links – Graphical representation of calls of tower
- Outgoing Calls – Outgoing calls of tower
- Incoming Calls – Incoming calls of tower
- Outgoing SMS – Outgoing SMS of tower
- Incoming SMS – Incoming SMS of tower
Tower groups can be made by location wise, case wise, date wise etc. as per requirement for further analysis.
- Group Details – Details of towers in a group
- Summary – Calls summary of a group
- Under Group Calls – Such calls where both numbers were present at same tower group
- Target and IMEI – Target numbers in a group using more than one handset
- IMEI and Target – IMEIs in a group using more than one sim card
- One to One Calling – Calling between specific two numbers only in a group
- Common Mobile Number – Common mobile numbers between different tower groups
- Common IMEI – Common IMEI between different tower groups
- Common Other Party – Common other party between different tower groups
- Common IMSI – Common IMSI between different tower groups
- Split Analysis – Analysis of calls of tower groups in different independent time frames
- Sub Groups – Analysis of calls of tower groups further dividing into small sub groups in different independent time frames
- Day wise Watch – Day wise common numbers in tower group
- Half Day wise Watch – Half day wise common numbers in tower group
- Internal Numbers In Group – Numbers in contact with different tower groups by being present at tower group or by making call from outside to tower group
- Internal Calls – Internal calls between different towers
- Pattern Analysis – Calls pattern of tower group
- Custom Pattern – Custom calling pattern of tower group
- Links – Graphical representation of calls of tower group
- Outgoing Calls – Outgoing calls of tower group
- Incoming Calls – Incoming calls of tower group
- Outgoing SMS – Outgoing SMS of tower group
- Incoming SMS – Incoming SMS of tower group
